User-Centric Digital Identity
Empowering you with trust, privacy, and simplicity.
We are building a future in which users truly own their digital identity.
Identity.com App
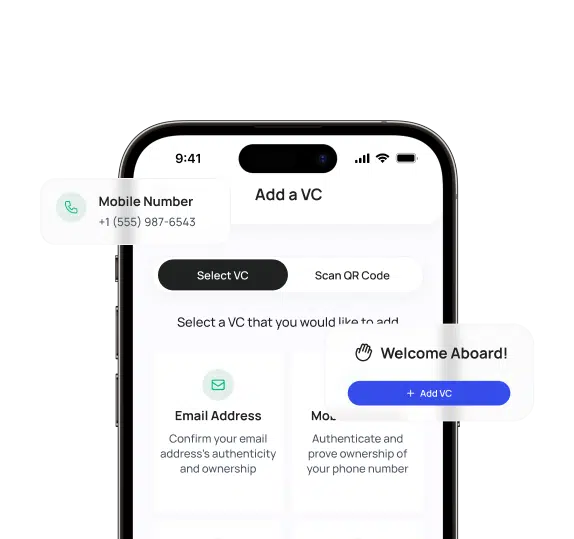

Add VC's to your library
Request VC’s from trusted authorities to verify specific attributes about you, like your age, profession, or education.
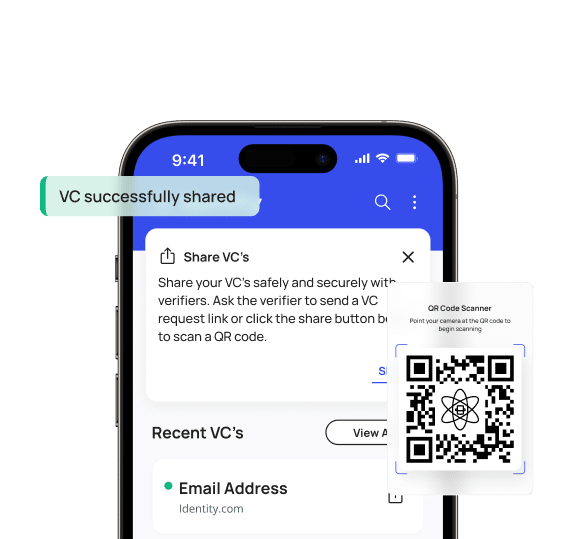
Share your VC’s with trusted intermediaries
Decide who sees your VC’s and which details to reveal. Verify once, share on your terms. Easily revoke access anytime.
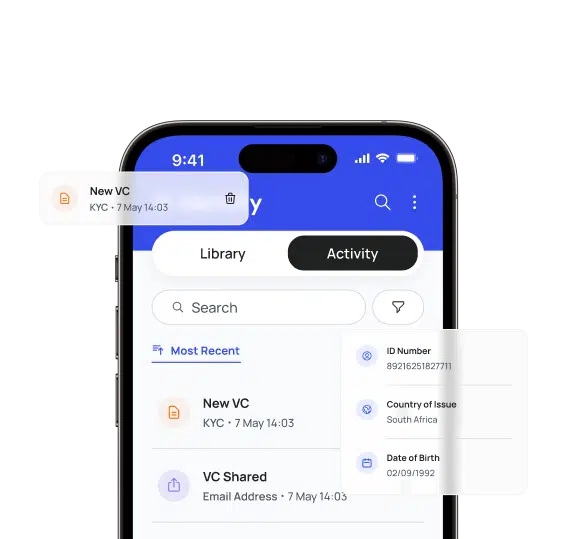
Manage your digital identity in one place
Make managing your digital identity convenient, private and fully controlled by you.
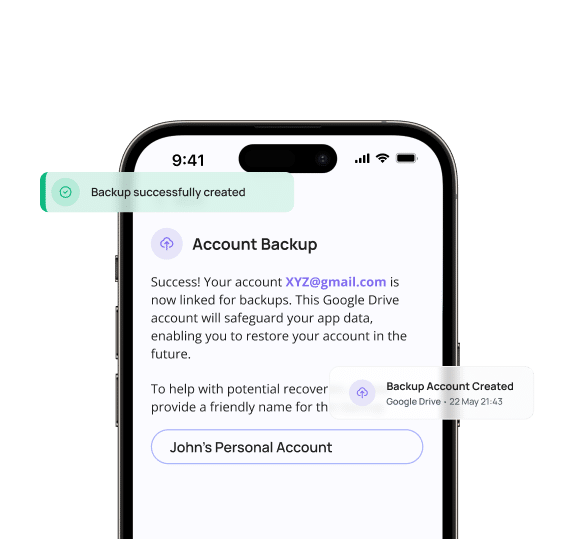
Backup & recover your account
Developer Tools
Leverage our open-source tools that bridge off-chain identities with on-chain interactions.
Gateway Protocol
Easily integrate dApp identity checks. With Gatekeeper Networks, users obtain Gateway Passes, streamlining identity requirements.
did:sol
Your Universal Digital ID.
Use one DID for all online interactions. Reliable, secure, and universal.
Cryptid
Wallets Redefined.
Merge real-world identity (via DIDs) with on-chain actions. Enhance security and incorporate dynamic logic for flexible blockchain interactions.
Our Associations





Frequently Asked Questions
Identity.com is a decentralized, open-source identity verification platform committed to providing users with secure, private, and user-friendly tools to verify and manage their identities online.
To bring trust, privacy, and simplicity to digital identity.
When the internet first began, there was no reliable way to verify who or what you were connecting with—much like meeting a stranger without any context.
Today, with billions of devices and people online, verifying identities has become essential for many activities. The lack of trusted identity verification is now a major source of cybercrime and online challenges. Identity.com tackles these issues by offering a secure and convenient way to verify identities online, reducing friction and enhancing trust.
The core technologies behind Identity.com and self-sovereign identity include:
- Decentralized Identifiers (DIDs): DIDs are unique identifiers that are globally resolvable and independent of any central authority. They are used to identify individuals and organizations in a decentralized network.
- Verifiable Credentials: Verifiable credentials are a type of digital credential that can be issued and verified by different entities in a decentralized network. These credentials can be used to prove a person’s identity, qualifications, or other attributes, and can be selectively disclosed to third parties without revealing any unnecessary information.
- Blockchain: Blockchain is a decentralized ledger technology that securely records transactions across multiple computers, ensuring transparency and immutability. It guarantees that once identity claims are issued and verified by trusted parties, they cannot be altered. This creates a tamper-proof and transparent system for managing digital identities.
- Identity wallets: Identity wallets are software applications that store an individual’s verifiable credentials and DIDs. These wallets allow individuals to manage their digital identity, selectively disclose their credentials, and control the sharing of their personal data.
Decentralized identity allows you to control who has access to your personal data and how it is used. You can choose which verifiable credentials to share with others and can revoke access at any time if you no longer want to share your data. Having your data stored on a decentralized network makes it harder for hackers to access it without your permission.











