Table of Contents
Introduction to IIW
Internet Identity Workshop (IIW) is a biannual event that has been at the forefront of identity discussions since 2005. Taking place at the Computer History Museum in Mountain View, CA, IIW’s “Open Space un-Conference” format fosters natural conversations, networking, and collaborative learning.
The attendees develop its format, free of traditional presentations, to share and discuss anything related to identity. The IIW is a great place to stay up-to-date with the latest identity trends and technical advancements.
Discussion Board at IIW Crafted by Attendees
Overarching Themes
Collaboration and Interoperability
Collaboration was a key theme, with discussions focusing on bridging gaps and enhancing interoperability. The vision is a cohesive global identity framework that can seamlessly integrate various technologies and platforms. This involves maturing protocols, aligning them with new standards, and ensuring that different identity solutions can work cohesively. One notable outcome of such collaboration is the improved interoperability between Verifiable Credential (VC) providers and digital wallets.
User-Centric Approach
Beyond technical details, there was an emphasis on end-user experience. The consensus was clear: identity systems of the future should be designed with the user in mind. Users should feel in control of their digital identities, with systems offering a seamless experience that doesn’t compromise security or privacy.
Building on Foundations
Several established companies were present, indicating an interest in understanding and adopting these evolving identity standards. This suggests a desire to integrate new identity protocols on top of existing Web2 infrastructures. Furthermore, there was an emphasis on education throughout different industries, including the next generation at a university level, introducing them to concepts such as Web3, DIDs, and decentralized technologies such as blockchain-based ledgers.
Key Discussions at IIW
Discussion Circle at IIW
The Progression of Identity Protocols: OpenID4VC and DIDComm
Identity.com explored the latest developments in identity protocols at IIW, including OpenID4VC and DIDComm.
OpenID4VC, which is tailored for presenting Verifiable Credentials, is gaining significant traction, especially with the backing of the EU. The discussion highlighted that this protocol closely relates to other popular OpenID protocols, and the EU now strongly supports it. In fact, the European Commission has issued guidelines that recommend the use of OpenID4VC for verifiable credential issuance and presentation.
DIDComm, which is rooted in Decentralized Identifiers (DIDs), offers a versatile solution for secure and private communication within the digital identity realm. Sam Curren’s session explored how DIDComm could augment OpenID4VC, hinting at a collaborative future for identity protocols. Its design makes it more versatile than OpenID4VC, supporting local peer-to-peer use cases with Bluetooth and NFC to come.
Digital Security and Verification
Digital security and verification were also key topics at IIW.
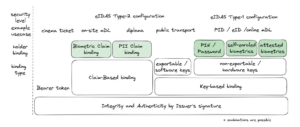
BIP32, which facilitates the creation of multiple cryptographic keys from a single seed, emerged as a pivotal topic. BIP32 enhances security and flexibility in digital transactions, especially when combined with FIDO keys. FIDO keys set the benchmark for enhanced authentication processes, safeguarding users’ digital identities against potential threats.
The eIDAS requirements, which set the standards for electronic identification in the European Single Market, were another highlight. The eIDAS requirements emphasize the importance of strong authentication and secure communication in protecting digital identities. Hardware-based keys, seamlessly integrated into devices, offer a robust security layer that meets the eIDAS requirements.
There was also a strong emphasis on the need for secure protocols surrounding digital identity documents. These protocols ensure that identity documents are created, issued, and verified with the highest standards of integrity and confidentiality. Some examples of secure protocols include digital signatures and encryption.
Lastly, there were discussions highlighting the various assurance levels in verifiable credentials. VCs use assurance levels to indicate the level of confidence that can be placed in the verification of an individual’s identity. The different assurance levels in VCs are based on the types of evidence that are used to verify an individual’s identity. For example, a VC with a high assurance level might require the user to provide a government-issued ID and a biometric authentication scan.
User Binding in Depth by IDunion
Collaboration and Standardization in Digital Identity
Emphasizing collaboration and standardization, Identity.com engaged in discussions around the W3C CCG DID Method Registry.
Led by our team member, Martin Riedel, the session aimed to refine the DID Method Registry. Participants brought up topics such as the potential deprecation of DID methods, regular liveliness checks, and multiple registrations under a single namespace. These discussions underscored our dedication to fostering a robust and standardized identity framework.
Additionally, we attended a session called “Verifiable Government through Citizen-Controlled Digital Identity“. This session discussed innovative digital identity strategies that aren’t anchored in blockchain. A primary focus was achieving seamless interoperability among diverse state regulators. One intriguing concept that emerged was the autonomic identifier, a form of digital identity owned by citizens through private key ownership. This approach paves the way for states to validate and endorse specific aspects of an individual’s identity, such as the authentication steps for obtaining a driver’s license. For example, you could use an autonomic identifier to prove that you are over the age of 21 and possess a valid driver’s license without revealing any other personal information.
Identity.com’s Perspective
At Identity.com, we are in the process of developing our Identity App, which is a digital ID app that allows you to request, store, and share verifiable credentials. Verifiable credentials are a new way to prove one’s identity without revealing sensitive personal information.
The insights and discussions from IIW have given us a deeper understanding of the evolving identity landscape and the needs of users. With this knowledge, we strive to ensure that our Identity App and technology embody the principles of trust, privacy, and simplicity. Providing a user-centric digital identity solution that is accessible to all.
Conclusion
The 37th IIW highlighted the evolving identity landscape and the importance of collaboration, innovation, and standardization in building a secure and user-centric digital identity ecosystem.
We are optimistic about the future of digital identity, where technology and user experience go hand in hand to craft a secure, seamless, and user-centric landscape.