Table of Contents
Each year, the Internet of Identity Workshop (IIW) stands out due to its unique operational format. Unlike typical conferences with pre-planned sessions, IIW allows attendees to choose the topics for each session on the day itself. This approach not only puts attendees at the forefront of trending discussions in the identity space but also encourages active participation. At IIW, you can listen to others, pitch your own ideas, and connect with fellow identity experts.

By regularly attending IIW, you begin to build meaningful connections and continue discussions from previous events, such as last fall’s IIW 37. During the three days we attended, from April 16th to April 18th at the Computer History Museum in Mountain View, California, discussions were rich with insights into content authenticity, the growing influence of AI, technical standards, regulations, and more. In this blog, we will dive deeper into the key themes we experienced at this past IIW, broken down by day.
Day 1: Content Authenticity and Personal AI Agents
Content Authenticity with C2PA
The first day of IIW began with an engaging presentation by Eric Scouten from Adobe, focusing on the Coalition for Content Provenance and Authenticity (C2PA). This initiative is crucial as it tackles the growing concerns about digital content authenticity, a problem caused by the widespread spread of misinformation online. Eric’s presentation outlined the C2PA framework, highlighting how it ensures the integrity and origin of digital content through manifest data models. This session emphasized the urgent need for robust mechanisms to authenticate content at its source.
SD-JWTs and Their Impact
Another highlight was the discussion on Signed Data JSON Web Tokens (SD-JWTs). Recongnized as a vital tool in securing digital identities, SD-JWTs ensure that data exchanged between parties maintains its integrity and authenticity. The session explored how SD-JWTs could be integrated within various identity frameworks, potentially revolutionizing the management and verification of digital identities in secure environments.
Exploring Personal AI Agents
The discussion on personal AI agents was particularly intriguing, examining how these agents could act autonomously on behalf of individuals, managing various aspects of digital identity and privacy. The potential for AI agents to streamline interactions in digital spaces without compromising security offers a glimpse into a future where technology could further personalize our digital experiences.
Day 2: Advanced Topics and Industry Engagement
Integrating Authenticity and Security in Digital Communications
Building on the previous day’s discussions, day 2 dived deeper into how identity information can be seamlessly integrated within C2PA manifests. The session explored the technical aspects of embedding verifiable credentials (VCs) and trust anchors, which are critical for establishing a reliable framework for content authenticity. This process involves the meticulous structuring of claims, the validation of these claims through signatures, and supporting these with assertions—all critical elements depicted in the C2PA Manifest graphic displayed below.
Diagram showing a C2PA Manifest and its constituent parts.
Expanding the Utility of Decentralized Technologies
The exploration of Decentralized Web Nodes (DWN) underscored a significant shift towards more robust and versatile identity management frameworks. DWNs facilitate a variety of decentralized applications, from simple note-taking apps to more complex social media platforms like those resembling Medium or Twitter. This session showcased the potential of decentralized technologies to support dynamic protocol implementation and offer scalable solutions across diverse digital landscapes.
Fostering Standardization and Collaboration
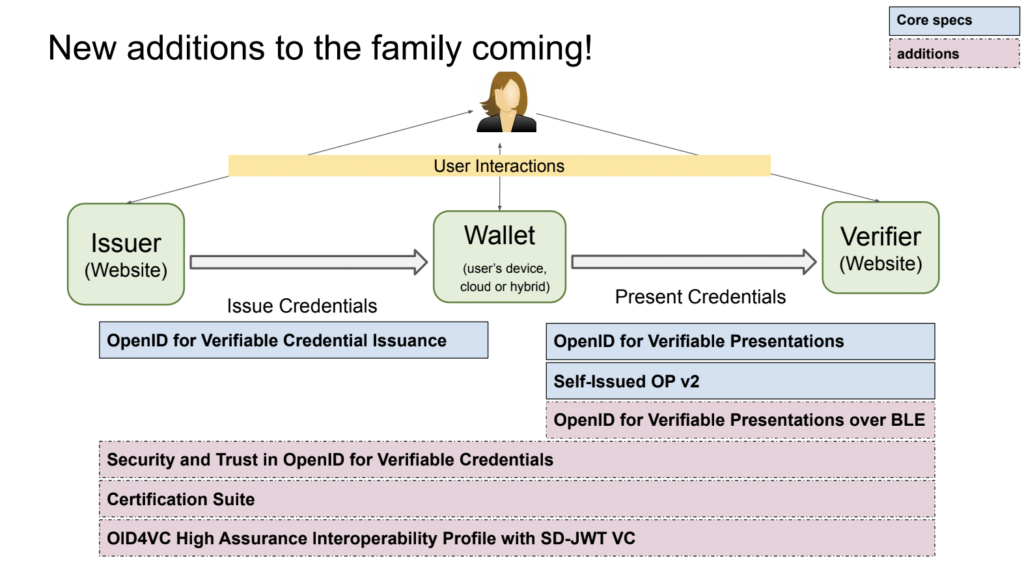
A central theme of the day focused on the concerted effort to standardize digital identity technologies and protocols. The OpenID4VP session showcased new features aimed at enhancing privacy and security, including capability negotiation and a new browser API. This underscored the protocol’s role in creating a developer-friendly ecosystem.
Diagram taken from OpenID4VP slide deck.
Furthermore, the “Navigating the Credential MAZE with DIF” session, featuring participation from our team member, Martin Riedel, introduced new initiatives to standardize credential schemas. These efforts by the Decentralized Identity Foundation (DIF) and the Claims and Credentials Group are designed to harmonize identity verification practices across the industry, aiming to reduce fragmentation and pave the way for more unified solutions.
Additionally, a notable demonstration by representatives from Apple and Google highlighted the interoperability between their respective wallets via a browser, marking a significant step in the industry’s technology integration. This demonstration challenged the ongoing value of third-party wallets by illustrating a trend towards government-issued credentials being managed within official wallets, raising questions about the role of third-party wallets for more personal or specific use-cases. At Identity.com, we are currently developing a mobile app that will allow you to manage your digital identity securely and be able to share digital credentials privately.
Day 3: Bridging Current Systems and Pioneering Future Solutions
Enhancing Interoperability in Identity Systems
The OpenID4VP/Presentation Exchange session focused on enhancing the framework for identity verification. Key suggestions included simplifying the query format and optimizing the interoperability of different verifiable credential (VC) data formats within the Presentation Exchange. This discussion highlights ongoing efforts to streamline and improve the efficiency of identity verification systems, making them more accessible and user-friendly across diverse platforms.
Integrating Traditional and Decentralized Identity Models
A session titled “A Bridge to the Future: Connecting X.509 and DIDs/VIDs,” explored the potential for integrating traditional X.509 infrastructure with decentralized identifiers (DIDs). It addressed the technical and conceptual challenges of merging these systems, illustrating the innovative approaches needed to harmonize conventional and modern identity frameworks. This theme captures the evolving nature of identity verification technologies and the push towards a more cohesive digital identity ecosystem.
Expanding and Standardizing Personal Identity Solutions
Day 3 also featured insightful sessions on personal identity management, such as the “Personal Data Store Faceoff” and an update on the EU Digital Identity (EUDI) Wallet under eIDAS 2. The faceoff session provided a detailed comparison of existing personal data storage solutions, highlighting their unique features and potential for future developments.
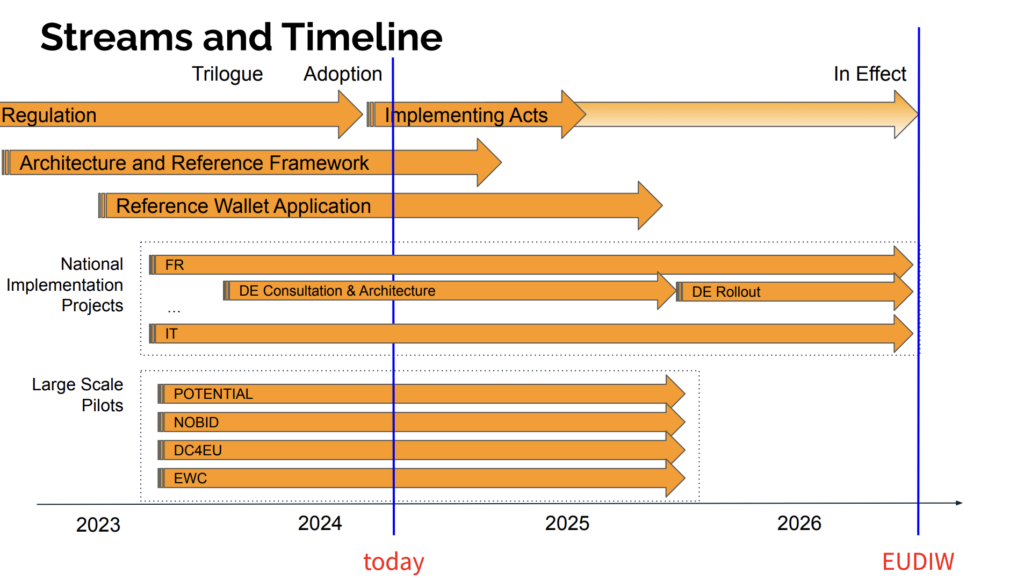
Additionally, the updates on the EUDI Wallet reviewed progress and outlined future plans, including an innovation competition designed to foster the creation of innovative prototypes in Germany. These discussions underscore the commitment to developing standardized, secure, and user-centered personal identity solutions across Europe.
eIDAS 2.0 Streams and Timeline
Key Themes and Insights
This year’s IIW highlighted several key themes:
- Content Authenticity: With the increasing capabilities of digital manipulation and the rise of deepfakes, robust content authenticity mechanisms such as C2PA are becoming increasingly important. We anticipate the development of more solutions designed to mitigate the risks associated with AI and prevent the creation of fake identities.
- Evolving Standards: The continuous refinement of standards, including OpenID4VP and eIDAS 2.0 with the EU Digital Identity Wallet, along with the integration of traditional and decentralized identity verification methods, underscores the dynamic evolution of the field.
- Big Tech Companies Transitioning to Decentralized Identity: Apple and Google’s collaborative session on cross-device verifiable credentials showcased how major tech companies are leading the shift toward decentralized identity systems, potentially accelerating broader adoption.
Implications and Future Trends
The discussions at IIW have significant implications for the digital identity landscape, indicating a shift toward more secure, efficient, and user-centric solutions. The active involvement of major tech companies highlights their important role in shaping industry standards.
Predictions for Future Trends:
- Increased Use of Verifiable Credentials: As AI advances and the need for privacy-preserving identity verification grows, verifiable credentials are expected to become more prevalent.
- Greater Industry Consolidation: Efforts to unify trust registries and standardize protocols will likely streamline operations, leading to more efficient identity management systems.
- Enhanced User Control and Privacy: Continuous improvements in standards and technologies are prioritizing enhanced control over personal data and security for users, fostering a more trustful digital environment.